白話物聯網安全(五):公網數據下的IoT
白話物聯網安全系列文章:
前提回顧
第一章《什么是物聯網的信息安全”》,我們講了什么物聯網,包含了哪幾方面的東西,物聯網的信息安全會涉及到什么,第二章《物聯網的安全檢測》,我們從一個IoT漏洞自動化利用工具AutoSploit講起,講到我們該如何檢測我們常見的物聯網存在的安全問題。第三章《IoT設備的安全防御》,我們從三個方向去談了IoT設備的安全,物理,近場和遠程,和現在市場上缺少的物聯網安全防御體系。第四章,我們探討一個概念性的話題,泛在物聯網,在這個基礎上我們在試試站在甲方爸爸的角度上談一談泛在物聯網的安全怎么做。
第五章,站在公網的數據角度上我們來看看現在的IoT安全。
正文:公網數據下的IoT
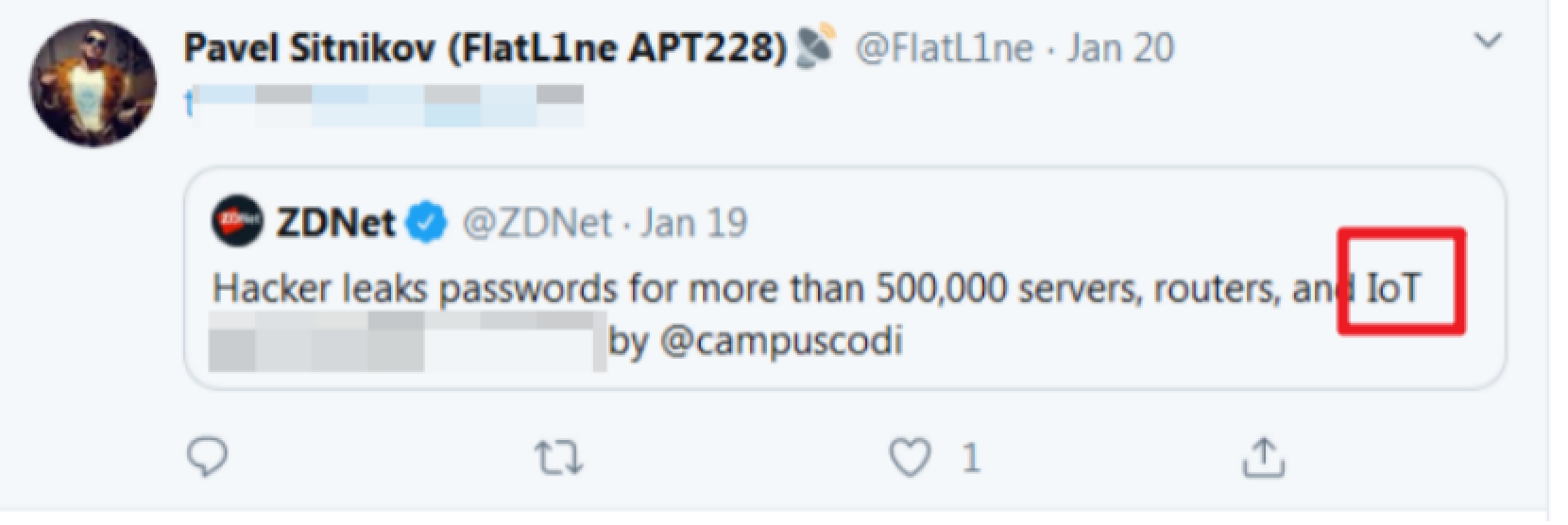
分析IoT數據之前,先簡單說近期的一個安全事件,2020年1月底,APT228組織爆出來50萬被攻擊IP地址,交換機,路由器,物聯網設備都有,國內國外都有,地址賬號密碼,擼了一份回來后,共16個txt文件,14M的文件,嘖嘖嘖,14M的txt文件。
圖:消息信息
圖:泄露數據
圖:部分數據截圖
(互聯網分析很多了,我這就不給各位大佬獻丑了)
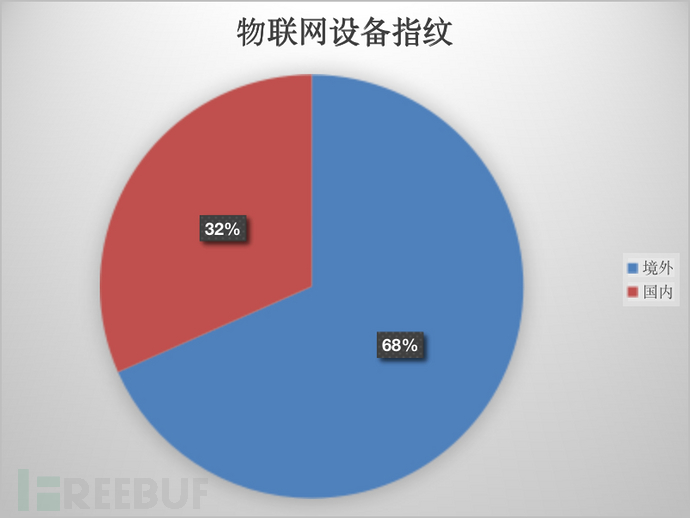
工欲善其事必先利其器,我們的先來看看現在主流的IoT設備包含的品類,在各大檢索數據平臺上,我發現物聯網設備指紋共有1161條(數據來自互聯網,不是完全包含現有指紋信息),粗略統計了一下,國內和國外的指紋比例如下圖:
在這個基礎上,國內的指紋信息我拿過來分析了一下,發現了非常有意思的一個事情,現在物聯網平臺不僅集中在交通,物流,農業,運營商,工控,家居,還在電梯,消防,建筑,地質,氣象,畜牧,醫藥等等,甚至于義務商城都有一個自己的物聯網感控平臺,在我們生活的方方面面,其實已經被整個物聯網包圍著,出門的電梯,快遞的盒子,運送的蔬菜,晚餐里面的燉排骨,都夾著物聯網的應急,樹立了一下,國內的指紋的信息分布見下圖:
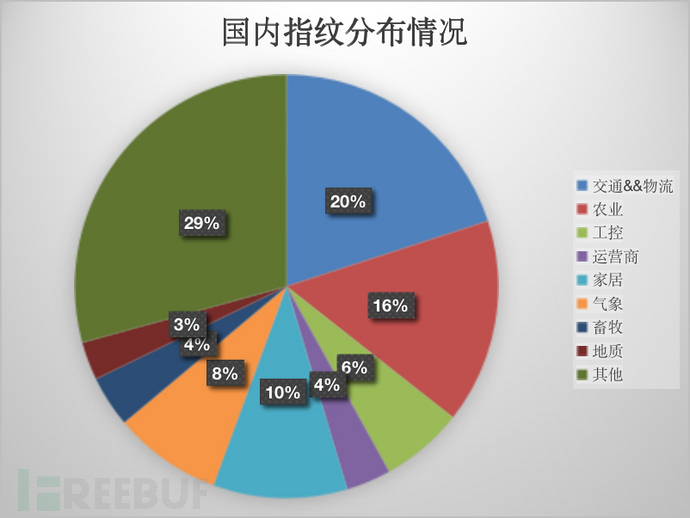
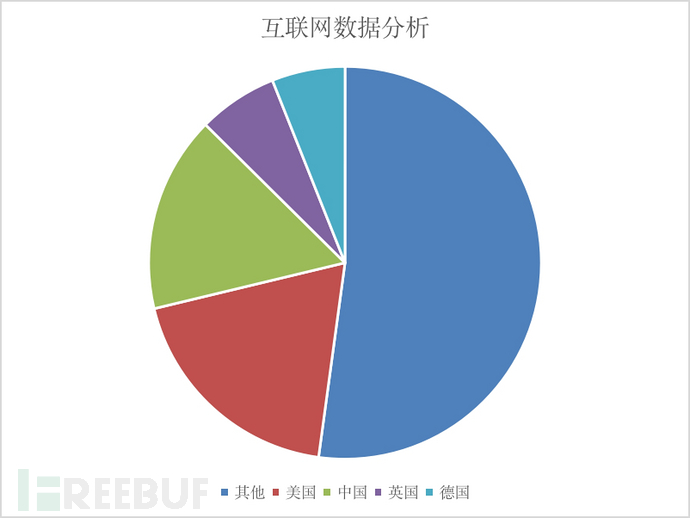
說完了指紋上面的事情,我們分析下物聯網設備在公網的開放情況,不可否認,絕大部分的物聯網設備其實都是內網環境,內網系統,公網上暴漏出來的甚少,比例甚至不到1%,基于有限的公網數據,咱們其實可以得出來一些簡單的結論,比如國家分布啊,端口,協議等等,現在能找到的數據為3,608,647條,美國最多,共計有683,415條,下來是中國,英國,法國,德國等等
通過分析,發現主要開放的端口為:80,443,8001,8080,8003,554,81,82,83,7547,22,21,23,5060,8080,49152,1024,8000,9002等等,主要涉及到的協議http,rtsp,https,http-proxy,telnet,irc,ftp,ssh,cwmp,sip等等,結合剛才我們說到的案例,其實物聯網設備的安全,還沒等提到挖掘漏洞,就已經被弱口令搞完了,隨便試了試,真的是一大堆,說句心里話,起碼改改12345這個密碼,舉個例子如下:
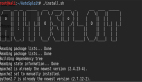
寫到這突然發現搞一個簡單的小腳本就可以實現批量的IoT弱口令探測,增加一個任意ip地址生成的腳本,然后探測存活(設計不合理,大佬輕噴),然后把地址扔給Hydra,在corntab設置Hydra定期執行,5分鐘執行一次
- def randomip():
- random=[]
- for i in range(4):
- random.append(randomom.randomint(0, 256))
- while True:
- if random[0] == 127 or random[0]==192 or random[0]==10 or random[0]==172:
- random[0]=randomom.randomrange(0, 256)
- else:
- break
- ipadd = '%d.%d.%d.%d' % (random[0], random[1], random[2], random[3])
- random.clear()
- return (ipadd)
最后放一個rapid7發出來的一些指紋信息和弱口令,大佬們想自己寫一個小腳本玩可以直接扔進去
- "axis":
- {
- "devTypePattern": [["body", "title"], ["regex", "(?i)axis", "(?i)camera"]],
- "loginUrlPattern": "document\\.write\\(\"([^\"\\]+)[^\\r\\n]+>Setup<\/a>",
- "auth": ["basic", "admin:admin"]
- },
- "mobotix": {
- "devTypePattern": [["body", ""], ["regex", "content=\"MOBOTIX AG"]],
- "nextUrl": ["string", "/control/userimage.html" ],
- "auth": ["basic", "admin:meinsm"]
- },
- "basler": {
- "devTypePattern": [["body", "title"], ["regex", "Basler AG"]],
- "nextUrl": ["string", "/cgi-bin/auth_if.cgi?Login" ],
- "auth": ["form", "", "Auth.Username=admin&Auth.Password=admin", "body", "regex", "success: true"]
- },
- "IQinVision": {
- "devTypePattern": [["body", ""], ["substr", "<meta name=\"author\" content=\"Brian Lau, IQinVision\">"]],
- "nextUrl": ["string", "/imageset.html" ],
- "auth": ["basic", "root:system"]
- },
- "JVC": {
- "devTypePattern": [["header", "server"], ["regex", "^JVC "]],
- "nextUrl": ["string", "/cgi-bin/c20display.cgi?c20encodeencode.html" ],
- "auth": ["basic", "admin:jvc"]
- },
- "SAMSUNG TECHWIN NVR": {
- "devTypePattern": [["body", "title"], ["==", "SAMSUNG TECHWIN NVR Web Viewer"]],
- "nextUrl": ["string", "/index.php/auth/login_confirm" ],
- "auth": ["form", "", "id=YWRtaW4%3D&pwd=2558a34d4d20964ca1d272ab26ccce9511d880579593cd4c9e01ab91ed00f325", "body", "substr", "\"is_login_ok\":2"]
- },
- "Sentry360": {
- "devTypePattern": [["header", "server"], ["==", "Sentry360 "]],
- "nextUrl": ["string", "/user.set?name=admin1&pwd=admin1&type=1" ],
- "auth": ["basic", "admin:1234"]
- },
- "Speco": {
- "devTypePattern": [["body", "title"], ["==", "Speco IP Camera"]],
- "nextUrl": ["string", "/httpapi?GetUserLevel&ipAddress=" ],
- "auth": ["basic", "admin:1234"]
- },
- "Stardot": {"comment": "",
- "devTypePattern": [["body", "title"], ["==", "NetCamSCD Live Image"]],
- "nextUrl": ["string", "/admin.cgi?0" ],
- "auth": ["basic", "admin:admin"]
- },
- "Toshiba eStudio": {
- "devTypePattern": [["body", "TITLE"], ["regex", "^TOSHIBA e.STUDIO"]],
- "nextUrl": ["string", "/cgi-bin/exportfile/printer/config/secure/settingfile.ucf" ],
- "auth": ["expect200"]
- },
- "Ubiquiti": {"comment": "",
- "devTypePattern": [["body", "title"], ["==", "EdgeOS"]],
- "nextUrl": ["string", "" ],
- "auth": ["form", "", "username=ubnt&password=ubnt", "body", "!substr", "form id=\"LoginForm\""]
- },
- "W-Box": {
- "devTypePattern": [["body", "title"], ["regex", "^W\\-BOX :"]],
- "nextUrl": ["string", "" ],
- "auth": ["form", "", "action=top&account=admin&password=wbox123&login=Login&parent_id=&app_path=", "body", "!substr", "input type=\"password\""]
- },
- "Brickcom": {
- "devTypePattern": [["header", "www-authenticate"], ["substr", "realm=\"Brickcom"]],
- "nextUrl": ["string", "" ],
- "auth": ["basic", "admin:admin"]
- },
- "Arecont": {
- "devTypePattern": [["header", "www-authenticate"], ["substr", "realm=\"Arecont Vision"]],
- "nextUrl": ["string", "" ],
- "auth": ["basic", ""]
- },
- "American Dynamics": {
- "devTypePattern": [["body", "title"], ["substr", "American Dynamics: Video Management Solutions"]],
- "nextUrl": ["string", "/video.htm" ],
- "auth": ["basic", "admin/admin"]
- },
- "ACTi": {
- "devTypePattern": [["body", "title"], ["substr", "Web Configurator - Version"]],
- "nextUrl": ["string", "/video.htm" ],
- "auth": ["form", "", "LOGIN_ACCOUNT=admin&LOGIN_PASSWORD=123456&LANGUAGE=0&btnSubmit=Login", "body", "!substr", ">Password<"]
- },
- "GeoVision": {
- "devTypePattern": [["header", "server"], ["==", "GeoHttpServer"]],
- "nextUrl": ["string", "/webcam_login" ],
- "auth": ["form", "", "id=admin&pwd=admin&ViewType=2&Login=Login", "body", "!substr", "<title>Invalid</title>"]
- },
- "Grandomstream": {
- "devTypePattern": [["body", "title"], ["==", "Grandomstream Device Configuration"]],
- "nextUrl": ["string", "/cgi-bin/dologin" ],
- "extractFormData": ["type=hidden value=(.*?)>"],
- "auth": ["form", "substitute", "P2=admin&LoginLogin=Login&gnkey=$1", "body", "!substr", "Your Login Password is not recognized"]
- }