"docker scan"本地掃描鏡像漏洞
Docker scan[1]本地掃描鏡像漏洞
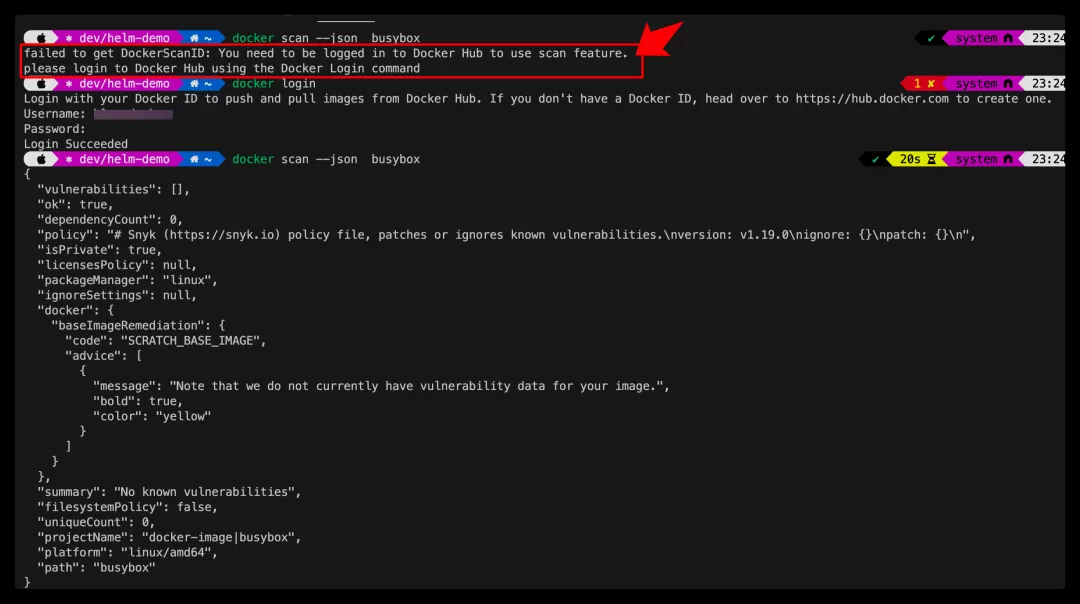
2020年年底,Docker hub推出鏡像自動掃描的功能,同時Docker也支持了在本地通過Docker命令選項的方式支持鏡像漏洞掃描,目前Docker Desktop for Mac以及window上的Docker都可以通過Docker scan子命令掃描本地鏡像是否存在漏洞軟件。
Docker Desktop For Mac
使用docker scan的時候需要登錄Docker Hub的賬號,同時docker scan支持一些不同的選項
- Options:
- --accept-license 接受使用第三方掃描提供商
- --dependency-tree 顯示帶有掃描結果的依賴樹
- --exclude-base 從漏洞掃描中排除基礎鏡像 (requires --file)
- -f, --file string 與image關聯的Dockerfile,提供更詳細的結果
- --group-issues 聚合重復的漏洞并將其分組為1個漏洞 (requires --json)
- --json 以json格式輸出結果
- --login 使用可選令牌(帶有--token)向掃描提供程序進行身份驗證,如果為空則使用web base令牌
- --reject-license 拒絕使用第三方掃描提供商
- --severity string 只報告提供級別或更高的漏洞(low|medium|high)
- --token string 登錄到第三方掃描提供程序的認證令牌
- --version 顯示掃描插件版本
指定Dockerfile
- $ docker scan -f Dockerfile docker-scan:e2e
- Testing docker-scan:e2e
- ...
- ✗ High severity vulnerability found in perl
- Description: Integer Overflow or Wraparound
- Info: https://snyk.io/vuln/SNYK-DEBIAN10-PERL-570802
- Introduced through: git@1:2.20.1-2+deb10u3, meta-common-packages@meta
- From: git@1:2.20.1-2+deb10u3 > perl@5.28.1-6
- From: git@1:2.20.1-2+deb10u3 > liberror-perl@0.17027-2 > perl@5.28.1-6
- From: git@1:2.20.1-2+deb10u3 > perl@5.28.1-6 > perl/perl-modules-5.28@5.28.1-6
- and 3 more...
- Introduced by your base image (golang:1.14.6)
- Organization: docker-desktop-test
- Package manager: deb
- Target file: Dockerfile
- Project name: docker-image|99138c65ebc7
- Docker image: 99138c65ebc7
- Base image: golang:1.14.6
- Licenses: enabled
- Tested 200 dependencies for known issues, found 157 issues.
- According to our scan, you are currently using the most secure version of the selected base image
不掃描該鏡像的基礎鏡像
- $ docker scan -f Dockerfile --exclude-base docker-scan:e2e
- Testing docker-scan:e2e
- ...
- ✗ Medium severity vulnerability found in libidn2/libidn2-0
- Description: Improper Input Validation
- Info: https://snyk.io/vuln/SNYK-DEBIAN10-LIBIDN2-474100
- Introduced through: iputils/iputils-ping@3:20180629-2+deb10u1, wget@1.20.1-1.1, curl@7.64.0-4+deb10u1, git@1:2.20.1-2+deb10u3
- From: iputils/iputils-ping@3:20180629-2+deb10u1 > libidn2/libidn2-0@2.0.5-1+deb10u1
- From: wget@1.20.1-1.1 > libidn2/libidn2-0@2.0.5-1+deb10u1
- From: curl@7.64.0-4+deb10u1 > curl/libcurl4@7.64.0-4+deb10u1 > libidn2/libidn2-0@2.0.5-1+deb10u1
- and 3 more...
- Introduced in your Dockerfile by 'RUN apk add -U --no-cache wget tar'
- Organization: docker-desktop-test
- Package manager: deb
- Target file: Dockerfile
- Project name: docker-image|99138c65ebc7
- Docker image: 99138c65ebc7
- Base image: golang:1.14.6
- Licenses: enabled
- Tested 200 dependencies for known issues, found 16 issues.
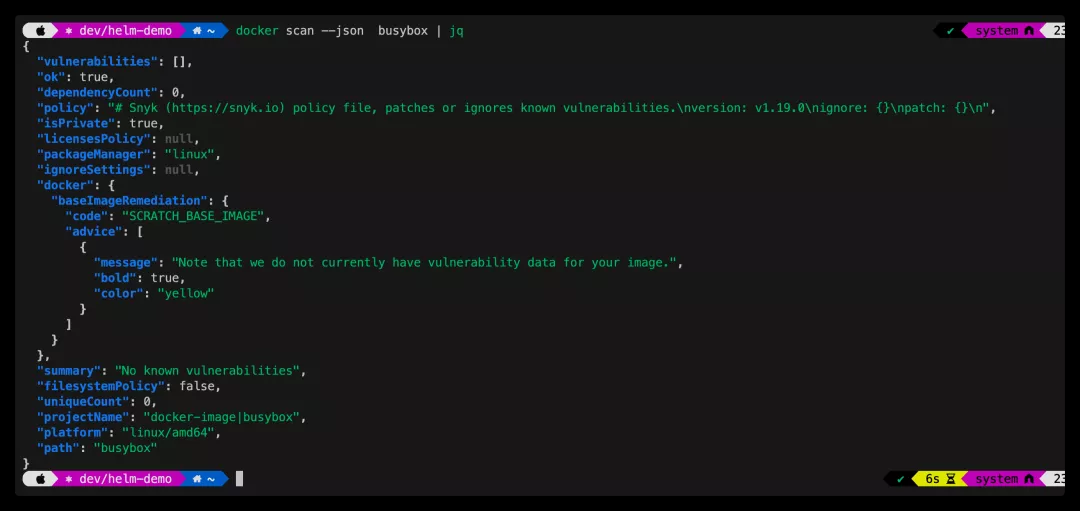
以json格式輸出掃描結果
JSON格式顯示鏡像掃描結果
聚合分組顯示掃描信息
- $ docker scan --json --group-issues docker-scan:e2e
- {
- {
- "title": "Improper Check for Dropped Privileges",
- ...
- "packageName": "bash",
- "language": "linux",
- "packageManager": "debian:10",
- "description": "## Overview\nAn issue was discovered in disable_priv_mode in shell.c in GNU Bash through 5.0 patch 11. By default, if Bash is run with its effective UID not equal to its real UID, it will drop privileges by setting its effective UID to its real UID. However, it does so incorrectly. On Linux and other systems that support \"saved UID\" functionality, the saved UID is not dropped. An attacker with command execution in the shell can use \"enable -f\" for runtime loading of a new builtin, which can be a shared object that calls setuid() and therefore regains privileges. However, binaries running with an effective UID of 0 are unaffected.\n\n## References\n- [CONFIRM](https://security.netapp.com/advisory/ntap-20200430-0003/)\n- [Debian Security Tracker](https://security-tracker.debian.org/tracker/CVE-2019-18276)\n- [GitHub Commit](https://github.com/bminor/bash/commit/951bdaad7a18cc0dc1036bba86b18b90874d39ff)\n- [MISC](http://packetstormsecurity.com/files/155498/Bash-5.0-Patch-11-Privilege-Escalation.html)\n- [MISC](https://www.youtube.com/watch?v=-wGtxJ8opa8)\n- [Ubuntu CVE Tracker](http://people.ubuntu.com/~ubuntu-security/cve/CVE-2019-18276)\n",
- "identifiers": {
- "ALTERNATIVE": [],
- "CVE": [
- "CVE-2019-18276"
- ],
- "CWE": [
- "CWE-273"
- ]
- },
- "severity": "low",
- "severityWithCritical": "low",
- "cvssScore": 7.8,
- "CVSSv3": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:F",
- ...
- "from": [
- "docker-image|docker-scan@e2e",
- "bash@5.0-4"
- ],
- "upgradePath": [],
- "isUpgradable": false,
- "isPatchable": false,
- "name": "bash",
- "version": "5.0-4"
- },
- ...
- "summary": "880 vulnerable dependency paths",
- "filesystemPolicy": false,
- "filtered": {
- "ignore": [],
- "patch": []
- },
- "uniqueCount": 158,
- "projectName": "docker-image|docker-scan",
- "platform": "linux/amd64",
- "path": "docker-scan:e2e"
- }
顯示指定級別的漏洞,只有高于此級別的漏洞才會顯示出來
- $ docker scan --severity=medium docker-scan:e2e
- ./bin/docker-scan_darwin_amd64 scan --severity=medium docker-scan:e2e
- Testing docker-scan:e2e...
- ✗ Medium severity vulnerability found in sqlite3/libsqlite3-0
- Description: Divide By Zero
- Info: https://snyk.io/vuln/SNYK-DEBIAN10-SQLITE3-466337
- Introduced through: gnupg2/gnupg@2.2.12-1+deb10u1, subversion@1.10.4-1+deb10u1, mercurial@4.8.2-1+deb10u1
- From: gnupg2/gnupg@2.2.12-1+deb10u1 > gnupg2/gpg@2.2.12-1+deb10u1 > sqlite3/libsqlite3-0@3.27.2-3
- From: subversion@1.10.4-1+deb10u1 > subversion/libsvn1@1.10.4-1+deb10u1 > sqlite3/libsqlite3-0@3.27.2-3
- From: mercurial@4.8.2-1+deb10u1 > python-defaults/python@2.7.16-1 > python2.7@2.7.16-2+deb10u1 > python2.7/libpython2.7-stdlib@2.7.16-2+deb10u1 > sqlite3/libsqlite3-0@3.27.2-3
- ✗ Medium severity vulnerability found in sqlite3/libsqlite3-0
- Description: Uncontrolled Recursion
- ...
- ✗ High severity vulnerability found in binutils/binutils-common
- Description: Missing Release of Resource after Effective Lifetime
- Info: https://snyk.io/vuln/SNYK-DEBIAN10-BINUTILS-403318
- Introduced through: gcc-defaults/g++@4:8.3.0-1
- From: gcc-defaults/g++@4:8.3.0-1 > gcc-defaults/gcc@4:8.3.0-1 > gcc-8@8.3.0-6 > binutils@2.31.1-16 > binutils/binutils-common@2.31.1-16
- From: gcc-defaults/g++@4:8.3.0-1 > gcc-defaults/gcc@4:8.3.0-1 > gcc-8@8.3.0-6 > binutils@2.31.1-16 > binutils/libbinutils@2.31.1-16 > binutils/binutils-common@2.31.1-16
- From: gcc-defaults/g++@4:8.3.0-1 > gcc-defaults/gcc@4:8.3.0-1 > gcc-8@8.3.0-6 > binutils@2.31.1-16 > binutils/binutils-x86-64-linux-gnu@2.31.1-16 > binutils/binutils-common@2.31.1-16
- and 4 more...
- Organization: docker-desktop-test
- Package manager: deb
- Project name: docker-image|docker-scan
- Docker image: docker-scan:e2e
- Platform: linux/amd64
- Licenses: enabled
- Tested 200 dependencies for known issues, found 37 issues.
Linux上安裝scan-cli插件
目前Linux系統上的Docker Engine尚未支持scan命令,因此可以通過插件形式使用,可以參考scan-cli-plugin[2]的文檔,此處我在Ubuntu上通過apt安裝一下
- > cat /etc/apt/sources.list.d/docker.list
- deb [arch=amd64] https://mirrors.aliyun.com/docker-ce/linux/ubuntu xenial stable
- > apt-get update && apt-get install docker-scan-plugin
安裝完成之后,登錄Docker hub,然后同意訪問Snyk即可。
參考資料
[1]docker scan:
https://docs.docker.com/engine/scan/
[2]scan-cli-plugin:
https://github.com/docker/scan-cli-plugin
本文轉載自微信公眾號「云原生生態圈」,可以通過以下二維碼關注。轉載本文請聯系云原生生態圈公眾號。