讓我們來(lái)看一下可用哪些方法來(lái)使用Xen 虛擬化技術(shù)降低成本、提高靈活性、簡(jiǎn)化管理并確保可靠的操作。我們將介紹在服務(wù)器整合、按需計(jì)算、高可用性計(jì)算和受管資源服務(wù)質(zhì)量 (QoS) 領(lǐng)域中使用 Xen 的數(shù)種方法。
1 說(shuō)明
所需軟件及下載地址
CentOS 5.2-----------------------------------------------------最穩(wěn)定的Linux服務(wù)器
ppp-2.4.3.tar.gz-----------------------------------------------PPP主程序
openssl-0.9.8i.tar.gz-----------------------------------------生產(chǎn)證書的主程序
xl2tpd-1.2.3.tar.gz--------------------------------------------FreeRadius服務(wù)器主程序
openswan-2.6.19.tar.gz-------------------------------------IPSec主程序
1.2 實(shí)現(xiàn)過(guò)程及功能特性
我們的試驗(yàn)網(wǎng)絡(luò)拓?fù)淙缦聢D所示:
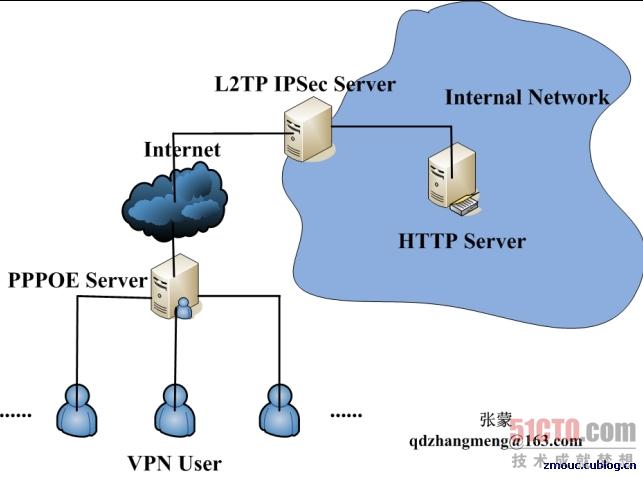
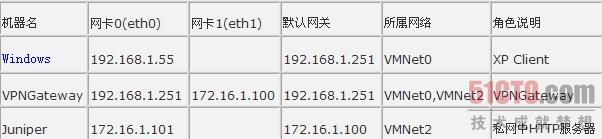
我們采用VM虛擬機(jī)試驗(yàn),VM中的網(wǎng)絡(luò)設(shè)置如下:
在VMware提供的Virtual Network Editor中的“Host Virtual Network Mapping”選項(xiàng)卡中,把VMNet2設(shè)為Not bridged,點(diǎn)擊右邊的“>”按鈕-subnet,IP地址填入172.16.1.0,確定。
VPNGateway虛擬機(jī)需要再添加一個(gè)網(wǎng)卡,然后在Linux下按照下表設(shè)置各個(gè)網(wǎng)卡,并在虛擬機(jī)設(shè)置中選擇網(wǎng)卡對(duì)應(yīng)的網(wǎng)絡(luò)。其中VPNGateway的網(wǎng)卡0屬于VMNet0,網(wǎng)卡1屬于VMNet2。網(wǎng)卡1的默認(rèn)網(wǎng)卡設(shè)為192.168.2.1。
另外,XP本機(jī)自動(dòng)位于VMNet0,不需要進(jìn)行設(shè)置。
其中,192.168.1.0/24網(wǎng)段模擬外網(wǎng),windows xp模擬外網(wǎng)撥號(hào)的VPN客戶機(jī)。
172.16.1.0/24網(wǎng)段模擬內(nèi)網(wǎng),Juniper為內(nèi)網(wǎng)中一臺(tái)機(jī)器,作為企業(yè)內(nèi)部的HTTP服務(wù)器。
#P#
2.架設(shè)服務(wù)器
具體過(guò)程不再贅述,相關(guān)配置文件如下:
|
OpenSWan 主要配置文件:
/etc/ipsec.secrets 用來(lái)保存private RSA keys 和 preshared secrets (PSKs)
/etc/ipsec.conf 配置文件(settings, options, defaults, connections)
OpenSWan 主要配置目錄 :
/etc/ipsec.d/cacerts 存放X.509 認(rèn)證證書(根證書-"root certificates")
/etc/ipsec.d/certs 存放X.509 客戶端證書(X.509 client Certificates)
/etc/ipsec.d/private 存放X.509 認(rèn)證私鑰(X.509 Certificate private keys)
/etc/ipsec.d/crls 存放X.509 證書撤消列表(X.509 Certificate Revocation Lists)
/etc/ipsec.d/ocspcerts 存放X.500 OCSP 證書(Online Certificate Status Protocol certificates)
/etc/ipsec.d/passwd XAUTH 密碼文件(XAUTH password file)
/etc/ipsec.d/policies 存放Opportunistic Encryption 策略組(The Opportunistic Encryption policy groups)
|
|
[root@mm ~]# cat /etc/ppp/chap-secrets # Secrets for authentication using CHAP #
client server secret IP addresses
test1 * test1 *
l2tptest1 * l2tptest1 10.1.1.1
l2tptest2 * l2tptest2 * |
|
[root@mm ~]# cat /etc/ipsec.secrets
RSA /etc/ipsec.d/private/vpngateway.key "123456"
#192.168.1.251 %any : PSK "123456" |
|
[root@mm ~]# cat /etc/ipsec.conf
#version 2.0
config setup
interfaces=%defaultroute
nat_traversal=yes
virtual_private=%v4:192.168.0.0/16,%v4:10.0.0.0/8,%v4:172.16.1.0/24,%v4:!192.168.1.0/24
conn %default
compress=yes
authby=rsasig
leftrsasigkey=%cert
rightrsasigkey=%cert
#conn roadwarrior
#left=172.16.1.100
#leftcert=vpngateway.cert
#leftsubnet=172.16.1.0/24
#right=%any
#auto=add
conn l2tpx509
pfs=no auto=add
left=192.168.1.251
leftcert=vpngateway.cert
leftprotoport=17/1701
right=%any
rightca=%same
rightprotoport=17/%any ############################################################################# #configure preshared secret authentication
#conn l2tp
# authby=secret
# pfs=no
# auto=add
# type=transport
# left=192.168.1.251
# leftprotoport=17/1701
# right=%any
# rightprotoport=17/%any ############################################################################# #include /etc/ipsec.d/examples/no_oe.conf |
|
[root@mm ~]# cat /etc/ppp/options.xl2tpd
ipcp-accept-local
ipcp-accept-remote
ms-dns 192.168.10.1
ms-dns 192.168.10.3
ms-wins 192.168.10.2
ms-wins 192.168.10.4
#noccp
auth
crtscts
idle 1800
mtu 1410
mru 1410
nodefaultroute
debug
lock
proxyarp
connect-delay 5000
logfile /var/log/l2tpd.log
proxyarp |
|
[root@mm ~]# cat /etc/xl2tpd/xl2tpd.conf
[global]
listen-addr = 192.168.1.251
port = 1701
auth file = /etc/ppp/chap-secrets
debug tunnel = yes
[lns default]
ip range = 172.16.1.10-172.16.1.254
local ip = 192.168.1.251
require chap = yes
refuse pap = yes
require authentication = yes
name = mm's L2TP VPN Server
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes |
|
復(fù)制證書(在機(jī)器之間復(fù)制證書請(qǐng)確保安全性):
#cp cacert.pem /etc/ipsec.d/cacerts
#cp vpngateway.cert /etc/ipsec.d/certs
#cp vpngateway.key /etc/ipsec.d/private
#cp crl.pem /etc/ipsec.d/crls/ |
|
CA工作目錄: /root/CA
# openssl req ‐x509 ‐days 3650 ‐newkey rsa:1024 ‐keyout cakey.pem ‐out cacert.pem
# mkdir newcerts
# touch index.txt
# echo "01" > serial
# echo "01" > crlnumber
# mkdir private
# cp cakey.pem ./private/
# openssl ca ‐gencrl ‐out crl.pem
# openssl req ‐newkey rsa:1024 ‐keyout vpngateway.key ‐out vpngatewayreq.pem
# openssl ca ‐in ../vpngatewayreq.pem ‐days 365 ‐out ../vpngateway.cert ‐notext
# openssl pkcs12 ‐export ‐in cacert.pem ‐inkey cakey.pem ‐out demoCA.p12
下面產(chǎn)生windows的私鑰及證書:
# openssl req ‐newkey rsa:1024 ‐keyout windows.key ‐out windowsreq.pem
# openssl ca ‐in ../windowsreq.pem ‐days 3650 ‐out ../windows.cert ‐notext
# openssl pkcs12 ‐export ‐in windows.cert ‐inkey windows.key ‐out windows.p12
注意,在導(dǎo)出P12文件時(shí),輸入讀取CA密鑰的密碼,然后再指定導(dǎo)出p12文件中的證書需要
的密碼,并進(jìn)行二次確認(rèn)。 |
#P#
用戶名l2tptest1,密碼l2tptest1,進(jìn)行撥號(hào),
可以看到獲得的IP 是/etc/ppp/chap‐secrets 文件中指定的那個(gè)IP:
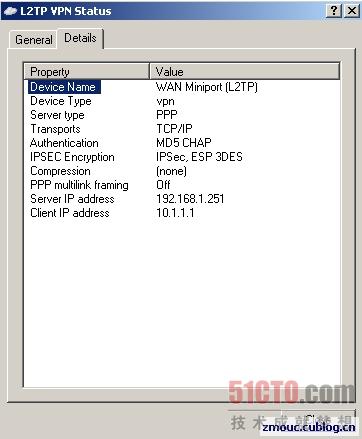
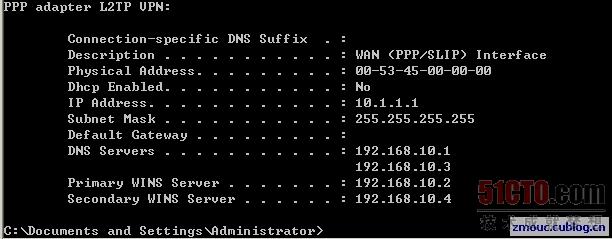
用戶名l2tptest2,密碼l2tptest2,進(jìn)行撥號(hào),
可以看到獲得的IP 是從地址池中獲得的:
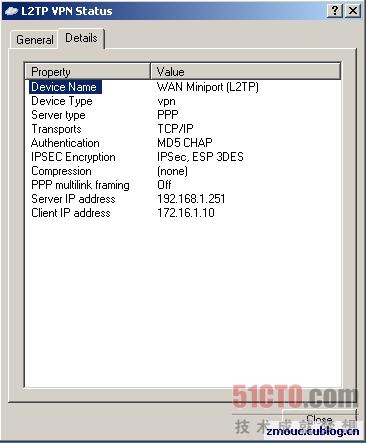
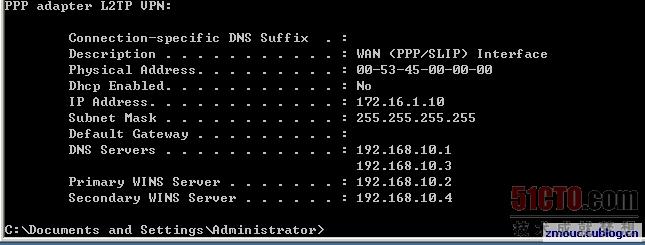
一個(gè)完整的撥號(hào)連接信息如下:
|
xl2tpd[7581]: build_fdset: closing down tunnel 34285
xl2tpd[7581]: get_call: allocating new tunnel for host 192.168.1.55, port 1701.
xl2tpd[7581]: get_call: allocating new tunnel for host 192.168.1.55, port 1701.
xl2tpd[7581]: control_finish: Peer requested tunnel 3 twice, ignoring second one.
xl2tpd[7581]: build_fdset: closing down tunnel 46042
xl2tpd[7581]: Connection established to 192.168.1.55, 1701. Local: 26849, Remote: 3 (ref=0/0).
LNS session is 'default'
xl2tpd[7581]: start_pppd: I'm running:
xl2tpd[7581]: "/usr/sbin/pppd"
xl2tpd[7581]: "passive"
xl2tpd[7581]: "‐detach"
xl2tpd[7581]: "192.168.1.251:172.16.1.10"
xl2tpd[7581]: "refuse‐pap"
xl2tpd[7581]: "auth"
xl2tpd[7581]: "require‐chap"
xl2tpd[7581]: "name"
xl2tpd[7581]: "mm's L2TP VPN Server"
xl2tpd[7581]: "debug"
xl2tpd[7581]: "file"
xl2tpd[7581]: "/etc/ppp/options.xl2tpd"
xl2tpd[7581]: "/dev/pts/1"
xl2tpd[7581]: Call established with 192.168.1.55, Local: 64654, Remote: 1, Serial: 0
xl2tpd[7581]: network_thread: select timeout
xl2tpd[7581]: network_thread: select timeout
xl2tpd[7581]: child_handler : pppd exited for call 1 with code 10
xl2tpd[7581]: call_close: Call 64654 to 192.168.1.55 disconnected
xl2tpd[7581]: control_finish: Connection closed to 192.168.1.55, port 1701 (), Local: 26849,
Remote: 3
xl2tpd[7581]: build_fdset: closing down tunnel 26849
xl2tpd[7581]: Trustingly terminating pppd: sending TERM signal to pid 7633
xl2tpd[7581]: pppd 7633 successfully terminated |
關(guān)于L2TP IPSec VPN 服務(wù)器的架設(shè),暫且學(xué)習(xí)到這里,其中還有很多細(xì)節(jié)需要學(xué)習(xí)和熟悉,有待進(jìn)一步的研究。
【編輯推薦】
- 玩轉(zhuǎn)linux之二-驅(qū)動(dòng)開發(fā)技術(shù)探析
- Linux設(shè)備驅(qū)動(dòng)開發(fā)詳解
- 嵌入式設(shè)備上的Linux系統(tǒng)開發(fā)
































