Windows Embedded下的網絡監測工具(二)
Ping命令
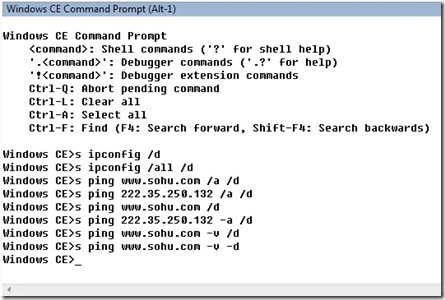
等Device Emulator啟動之后,我們可以在輸入命令進行調試了。在Target目錄中選Target Control,Command Shell會出現。下圖所示:
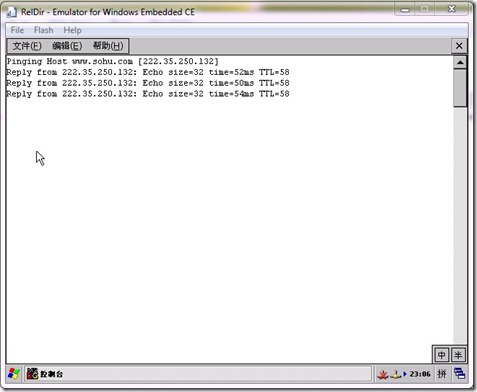
先運行ping命令,如果我們直接輸入s ping x.x.x.x的話,會在模擬器中顯示一個命令行窗口,并且輸出執行結果。S的意思是在CE中運行某個應用程序。結果如下圖:
不過問題隨之而來,命令行窗口會在ping命令執行完成后,自動退出。我們想查看ping命令的執行情況,就需要眼疾手快了。難道,沒有其他的辦法了嗎?
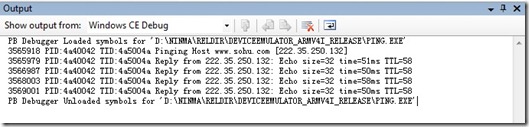
有,我們輸入s ping x.x.x.x /d,執行結果會輸出到output窗口中。
下面的演示我會將output里的結果貼出來,不再截圖了。
ipconfig命令
接下來是另外一個簡單的網絡監測工具:ipconfig。在Command Shell中輸入s ipconfig /all /d。/all 是ipconfig的命令,顯示所有的配置信息,除此之外還有/renew和/release兩個參數,用于更新網卡的IP地址。/d還是將結果顯示到 Output窗口中。
PB Debugger Loaded symbols for 'D:\NINMA\RELDIR\DEVICEEMULATOR_ARMV4I_RELEASE\IPCONFIG.EXE'
122396 PID:5860042 TID:5890056 Windows IP configuration
122465 PID:5860042 TID:5890056 Ethernet adapter Local Area Connection:
122465 PID:5860042 TID:5890056 IP Address ........ : 192.168.0.163
122465 PID:5860042 TID:5890056 Subnet Mask ....... : 255.255.255.0
122465 PID:5860042 TID:5890056 IP Address ........ : fe80::203:ffff:fe55:8d9f%5
122465 PID:5860042 TID:5890056 Default Gateway ... : 192.168.0.1
122465 PID:5860042 TID:5890056 Adapter Name ...... : NE20001
122465 PID:5860042 TID:5890056 Description ....... : NE20001
122465 PID:5860042 TID:5890056 Adapter Index ..... : 2
122465 PID:5860042 TID:5890056 Address............ : 00 03 ff 55 8d 9f
122465 PID:5860042 TID:5890056 DHCP Enabled....... : YES
122465 PID:5860042 TID:5890056 DHCP Server........ : 192.168.0.1
122465 PID:5860042 TID:5890056 Primary WinsServer :
122465 PID:5860042 TID:5890056 Secondary WinsServer:
122465 PID:5860042 TID:5890056 Lease obtained on : Sunday, July 5 ,2009 18 : 5 : 30
122465 PID:5860042 TID:5890056 Lease expires on : Sunday, July 12 ,2009 18 : 5 : 30
122465 PID:5860042 TID:5890056 AutoConfig Enabled : YES
122465 PID:5860042 TID:5890056
122465 PID:5860042 TID:5890056 Tunnel adapter []:
122467 PID:5860042 TID:5890056 Interface Number .. : 4
122467 PID:5860042 TID:5890056
122468 PID:5860042 TID:5890056 Tunnel adapter [6to4 Pseudo-Interface]:
122468 PID:5860042 TID:5890056 Interface Number .. : 3
122468 PID:5860042 TID:5890056
122469 PID:5860042 TID:5890056 Tunnel adapter [Automatic Tunneling Pseudo-Interface]:
122469 PID:5860042 TID:5890056 Interface Number .. : 2
122470 PID:5860042 TID:5890056 IP Address ........ : fe80::5efe:192.168.0.163%2
122470 PID:5860042 TID:5890056
122474 PID:5860042 TID:5890056 Host name.......... : WindowsCE
122474 PID:5860042 TID:5890056 Domain Name........ :
122474 PID:5860042 TID:5890056 DNS Servers........ : 62.244.19.19
122474 PID:5860042 TID:5890056 192.168.0.1
122474 PID:5860042 TID:5890056 NODETYPE........... : 8
122474 PID:5860042 TID:5890056 Routing Enabled.... : NO
122474 PID:5860042 TID:5890056 Proxy Enabled...... : NO
122474 PID:5860042 TID:5890056
PB Debugger Unloaded symbols for 'D:\NINMA\RELDIR\DEVICEEMULATOR_ARMV4I_RELEASE\IPCONFIG.EXE'
【編輯推薦】