實(shí)戰(zhàn)篇:Security+JWT組合拳
Good morning, everyone!
之前我們已經(jīng)說(shuō)過(guò)用Shiro和JWT來(lái)實(shí)現(xiàn)身份認(rèn)證和用戶(hù)授權(quán),今天我們?cè)賮?lái)說(shuō)一下「Security和JWT」的組合拳。
簡(jiǎn)介
先贅述一下身份認(rèn)證和用戶(hù)授權(quán):
用戶(hù)認(rèn)證(Authentication):系統(tǒng)通過(guò)校驗(yàn)用戶(hù)提供的用戶(hù)名和密碼來(lái)驗(yàn)證該用戶(hù)是否為系統(tǒng)中的合法主體,即是否可以訪(fǎng)問(wèn)該系統(tǒng);
用戶(hù)授權(quán)(Authorization):系統(tǒng)為用戶(hù)分配不同的角色,以獲取對(duì)應(yīng)的權(quán)限,即驗(yàn)證該用戶(hù)是否有權(quán)限執(zhí)行該操作;
Web應(yīng)用的安全性包括用戶(hù)認(rèn)證和用戶(hù)授權(quán)兩個(gè)部分,而Spring Security(以下簡(jiǎn)稱(chēng)Security)基于Spring框架,正好可以完整解決該問(wèn)題。
它的真正強(qiáng)大之處在于它可以輕松擴(kuò)展以滿(mǎn)足自定義要求。
原理
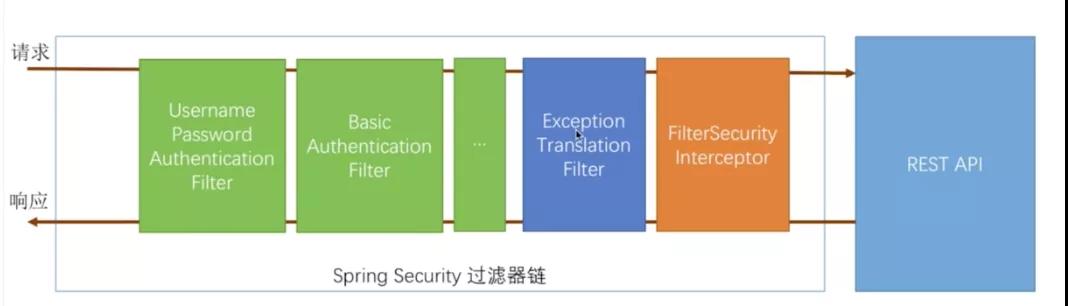
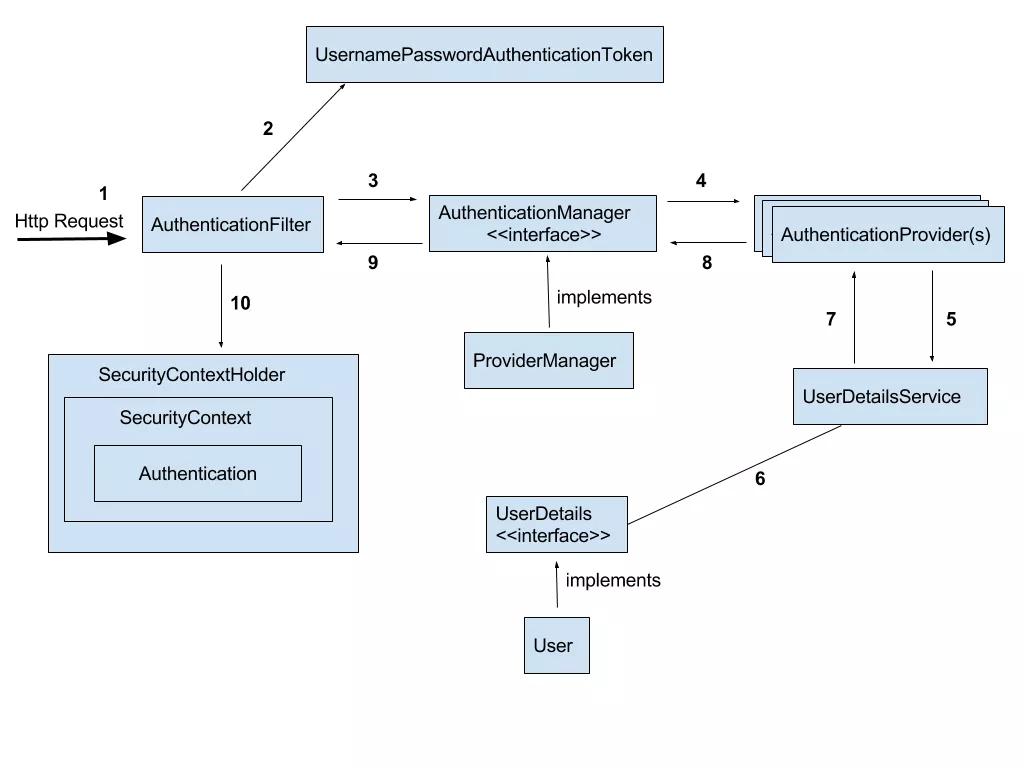
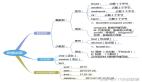
Security可以看做是由一組filter過(guò)濾器鏈組成的權(quán)限認(rèn)證。它的整個(gè)工作流程如下所示:
圖中綠色認(rèn)證方式是可以配置的,橘黃色和藍(lán)色的位置不可更改:
- FilterSecurityInterceptor:最后的過(guò)濾器,它會(huì)決定當(dāng)前的請(qǐng)求可不可以訪(fǎng)問(wèn)Controller
- ExceptionTranslationFilter:異常過(guò)濾器,接收到異常消息時(shí)會(huì)引導(dǎo)用戶(hù)進(jìn)行認(rèn)證;
實(shí)戰(zhàn)
項(xiàng)目準(zhǔn)備
我們使用Spring Boot框架來(lái)集成。
1.pom文件引入的依賴(lài)
- <dependency>
- <groupId>org.springframework.boot</groupId>
- <artifactId>spring-boot-starter</artifactId>
- </dependency>
- <dependency>
- <groupId>org.springframework.boot</groupId>
- <artifactId>spring-boot-starter-web</artifactId>
- <exclusions>
- <exclusion>
- <groupId>org.springframework.boot</groupId>
- <artifactId>spring-boot-starter-tomcat</artifactId>
- </exclusion>
- </exclusions>
- </dependency>
- <dependency>
- <groupId>org.springframework.boot</groupId>
- <artifactId>spring-boot-starter-undertow</artifactId>
- </dependency>
- <dependency>
- <groupId>mysql</groupId>
- <artifactId>mysql-connector-java</artifactId>
- </dependency>
- <dependency>
- <groupId>com.baomidou</groupId>
- <artifactId>mybatis-plus-boot-starter</artifactId>
- <version>3.4.0</version>
- </dependency>
- <dependency>
- <groupId>org.projectlombok</groupId>
- <artifactId>lombok</artifactId>
- </dependency>
- <!-- 阿里JSON解析器 -->
- <dependency>
- <groupId>com.alibaba</groupId>
- <artifactId>fastjson</artifactId>
- <version>1.2.74</version>
- </dependency>
- <dependency>
- <groupId>joda-time</groupId>
- <artifactId>joda-time</artifactId>
- <version>2.10.6</version>
- </dependency>
- <dependency>
- <groupId>org.springframework.boot</groupId>
- <artifactId>spring-boot-starter-test</artifactId>
- </dependency>
2.application.yml配置
- spring:
- application:
- name: securityjwt
- datasource:
- driver-class-name: com.mysql.cj.jdbc.Driver
- url: jdbc:mysql://127.0.0.1:3306/cheetah?characterEncoding=utf-8&useSSL=false&serverTimezone=UTC
- username: root
- password: 123456
- server:
- port: 8080
- mybatis:
- mapper-locations: classpath:mapper/*.xml
- type-aliases-package: com.itcheetah.securityjwt.entity
- configuration:
- map-underscore-to-camel-case: true
- rsa:
- key:
- pubKeyFile: C:\Users\Desktop\jwt\id_key_rsa.pub
- priKeyFile: C:\Users\Desktop\jwt\id_key_rsa
3.SQL文件
- /**
- * sys_user_info
- **/
- SET NAMES utf8mb4;
- SET FOREIGN_KEY_CHECKS = 0;
- -- ----------------------------
- -- Table structure for sys_user_info
- -- ----------------------------
- DROP TABLE IF EXISTS `sys_user_info`;
- CREATE TABLE `sys_user_info` (
- `id` bigint(20) NOT NULL AUTO_INCREMENT,
- `username` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
- `password` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
- PRIMARY KEY (`id`) USING BTREE
- ) ENGINE = InnoDB AUTO_INCREMENT = 3 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;
- SET FOREIGN_KEY_CHECKS = 1;
- /**
- * product_info
- **/
- SET NAMES utf8mb4;
- SET FOREIGN_KEY_CHECKS = 0;
- -- ----------------------------
- -- Table structure for product_info
- -- ----------------------------
- DROP TABLE IF EXISTS `product_info`;
- CREATE TABLE `product_info` (
- `id` bigint(20) NOT NULL AUTO_INCREMENT,
- `name` varchar(255) CHARACTER SET utf8 COLLATE utf8_general_ci NULL DEFAULT NULL,
- `price` decimal(10, 4) NULL DEFAULT NULL,
- `create_date` datetime(0) NULL DEFAULT NULL,
- `update_date` datetime(0) NULL DEFAULT NULL,
- PRIMARY KEY (`id`) USING BTREE
- ) ENGINE = InnoDB AUTO_INCREMENT = 4 CHARACTER SET = utf8 COLLATE = utf8_general_ci ROW_FORMAT = Dynamic;
- SET FOREIGN_KEY_CHECKS = 1;
引入依賴(lài)
- <dependency>
- <groupId>org.springframework.boot</groupId>
- <artifactId>spring-boot-starter-security</artifactId>
- </dependency>
- <!--Token生成與解析-->
- <dependency>
- <groupId>io.jsonwebtoken</groupId>
- <artifactId>jjwt</artifactId>
- <version>0.9.1</version>
- </dependency>
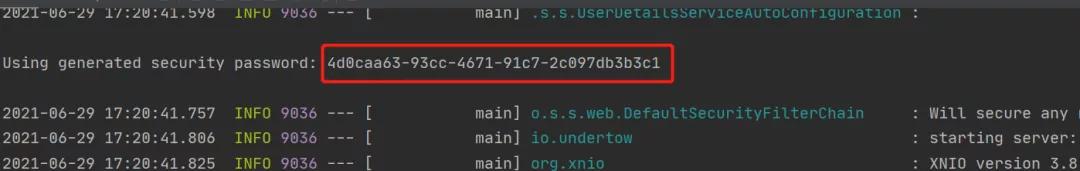
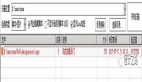
引入之后啟動(dòng)項(xiàng)目,會(huì)有如圖所示:
其中用戶(hù)名為user,密碼為上圖中的字符串。
SecurityConfig類(lèi)
- //開(kāi)啟全局方法安全性
- @EnableGlobalMethodSecurity(prePostEnabled=true, securedEnabled=true)
- public class SecurityConfig extends WebSecurityConfigurerAdapter {
- //認(rèn)證失敗處理類(lèi)
- @Autowired
- private AuthenticationEntryPointImpl unauthorizedHandler;
- //提供公鑰私鑰的配置類(lèi)
- @Autowired
- private RsaKeyProperties prop;
- @Autowired
- private UserInfoService userInfoService;
- @Override
- protected void configure(HttpSecurity httpSecurity) throws Exception {
- httpSecurity
- // CSRF禁用,因?yàn)椴皇褂胹ession
- .csrf().disable()
- // 認(rèn)證失敗處理類(lèi)
- .exceptionHandling().authenticationEntryPoint(unauthorizedHandler).and()
- // 基于token,所以不需要session
- .sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS).and()
- // 過(guò)濾請(qǐng)求
- .authorizeRequests()
- .antMatchers(
- HttpMethod.GET,
- "/*.html",
- "/**/*.html",
- "/**/*.css",
- "/**/*.js"
- ).permitAll()
- // 除上面外的所有請(qǐng)求全部需要鑒權(quán)認(rèn)證
- .anyRequest().authenticated()
- .and()
- .headers().frameOptions().disable();
- // 添加JWT filter
- httpSecurity.addFilter(new TokenLoginFilter(super.authenticationManager(), prop))
- .addFilter(new TokenVerifyFilter(super.authenticationManager(), prop));
- }
- //指定認(rèn)證對(duì)象的來(lái)源
- public void configure(AuthenticationManagerBuilder auth) throws Exception {
- auth.userDetailsService(userInfoService)
- //從前端傳遞過(guò)來(lái)的密碼就會(huì)被加密,所以從數(shù)據(jù)庫(kù)
- //查詢(xún)到的密碼必須是經(jīng)過(guò)加密的,而這個(gè)過(guò)程都是
- //在用戶(hù)注冊(cè)的時(shí)候進(jìn)行加密的。
- .passwordEncoder(passwordEncoder());
- }
- //密碼加密
- @Bean
- public BCryptPasswordEncoder passwordEncoder(){
- return new BCryptPasswordEncoder();
- }
- }
「攔截規(guī)則」
- anyRequest:匹配所有請(qǐng)求路徑
- access:SpringEl表達(dá)式結(jié)果為true時(shí)可以訪(fǎng)問(wèn)
- anonymous:匿名可以訪(fǎng)問(wèn)
- `denyAll:用戶(hù)不能訪(fǎng)問(wèn)
- fullyAuthenticated:用戶(hù)完全認(rèn)證可以訪(fǎng)問(wèn)(非remember-me下自動(dòng)登錄)
- hasAnyAuthority:如果有參數(shù),參數(shù)表示權(quán)限,則其中任何一個(gè)權(quán)限可以訪(fǎng)問(wèn)
- hasAnyRole:如果有參數(shù),參數(shù)表示角色,則其中任何一個(gè)角色可以訪(fǎng)問(wèn)
- hasAuthority:如果有參數(shù),參數(shù)表示權(quán)限,則其權(quán)限可以訪(fǎng)問(wèn)
- hasIpAddress:如果有參數(shù),參數(shù)表示IP地址,如果用戶(hù)IP和參數(shù)匹配,則可以訪(fǎng)問(wèn)
- hasRole:如果有參數(shù),參數(shù)表示角色,則其角色可以訪(fǎng)問(wèn)
- permitAll:用戶(hù)可以任意訪(fǎng)問(wèn)
- rememberMe:允許通過(guò)remember-me登錄的用戶(hù)訪(fǎng)問(wèn)
- authenticated:用戶(hù)登錄后可訪(fǎng)問(wèn)
認(rèn)證失敗處理類(lèi)
- /**
- * 返回未授權(quán)
- */
- @Component
- public class AuthenticationEntryPointImpl implements AuthenticationEntryPoint, Serializable {
- private static final long serialVersionUID = -8970718410437077606L;
- @Override
- public void commence(HttpServletRequest request, HttpServletResponse response, AuthenticationException e)
- throws IOException {
- int code = HttpStatus.UNAUTHORIZED;
- String msg = "認(rèn)證失敗,無(wú)法訪(fǎng)問(wèn)系統(tǒng)資源,請(qǐng)先登陸";
- ServletUtils.renderString(response, JSON.toJSONString(AjaxResult.error(code, msg)));
- }
- }
認(rèn)證流程
自定義認(rèn)證過(guò)濾器
- public class TokenLoginFilter extends UsernamePasswordAuthenticationFilter {
- private AuthenticationManager authenticationManager;
- private RsaKeyProperties prop;
- public TokenLoginFilter(AuthenticationManager authenticationManager, RsaKeyProperties prop) {
- this.authenticationManager = authenticationManager;
- this.prop = prop;
- }
- /**
- * @author cheetah
- * @description 登陸驗(yàn)證
- * @date 2021/6/28 16:17
- * @Param [request, response]
- * @return org.springframework.security.core.Authentication
- **/
- public Authentication attemptAuthentication(HttpServletRequest request, HttpServletResponse response) throws AuthenticationException {
- try {
- UserPojo sysUser = new ObjectMapper().readValue(request.getInputStream(), UserPojo.class);
- UsernamePasswordAuthenticationToken authRequest = new UsernamePasswordAuthenticationToken(sysUser.getUsername(), sysUser.getPassword());
- return authenticationManager.authenticate(authRequest);
- }catch (Exception e){
- try {
- response.setContentType("application/json;charset=utf-8");
- response.setStatus(HttpServletResponse.SC_UNAUTHORIZED);
- PrintWriter out = response.getWriter();
- Map resultMap = new HashMap();
- resultMap.put("code", HttpServletResponse.SC_UNAUTHORIZED);
- resultMap.put("msg", "用戶(hù)名或密碼錯(cuò)誤!");
- out.write(new ObjectMapper().writeValueAsString(resultMap));
- out.flush();
- out.close();
- }catch (Exception outEx){
- outEx.printStackTrace();
- }
- throw new RuntimeException(e);
- }
- }
- /**
- * @author cheetah
- * @description 登陸成功回調(diào)
- * @date 2021/6/28 16:17
- * @Param [request, response, chain, authResult]
- * @return void
- **/
- public void successfulAuthentication(HttpServletRequest request, HttpServletResponse response, FilterChain chain, Authentication authResult) throws IOException, ServletException {
- UserPojo user = new UserPojo();
- user.setUsername(authResult.getName());
- user.setRoles((List<RolePojo>)authResult.getAuthorities());
- //通過(guò)私鑰進(jìn)行加密:token有效期一天
- String token = JwtUtils.generateTokenExpireInMinutes(user, prop.getPrivateKey(), 24 * 60);
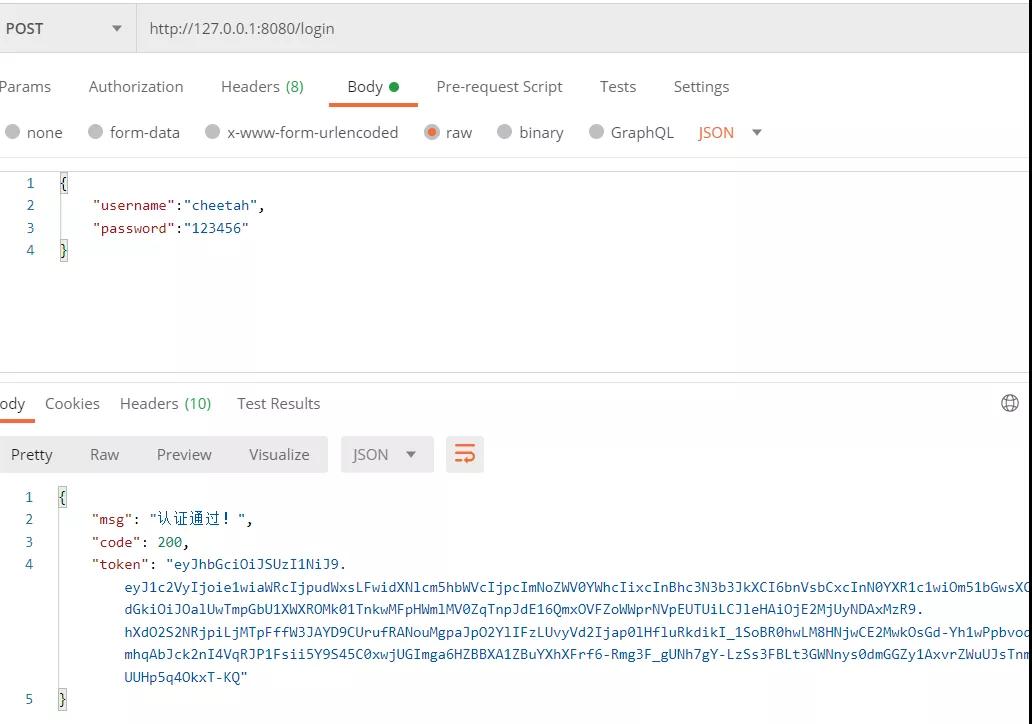
- response.addHeader("Authorization", "Bearer "+token);
- try {
- response.setContentType("application/json;charset=utf-8");
- response.setStatus(HttpServletResponse.SC_OK);
- PrintWriter out = response.getWriter();
- Map resultMap = new HashMap();
- resultMap.put("code", HttpServletResponse.SC_OK);
- resultMap.put("msg", "認(rèn)證通過(guò)!");
- resultMap.put("token", token);
- out.write(new ObjectMapper().writeValueAsString(resultMap));
- out.flush();
- out.close();
- }catch (Exception outEx){
- outEx.printStackTrace();
- }
- }
- }
流程
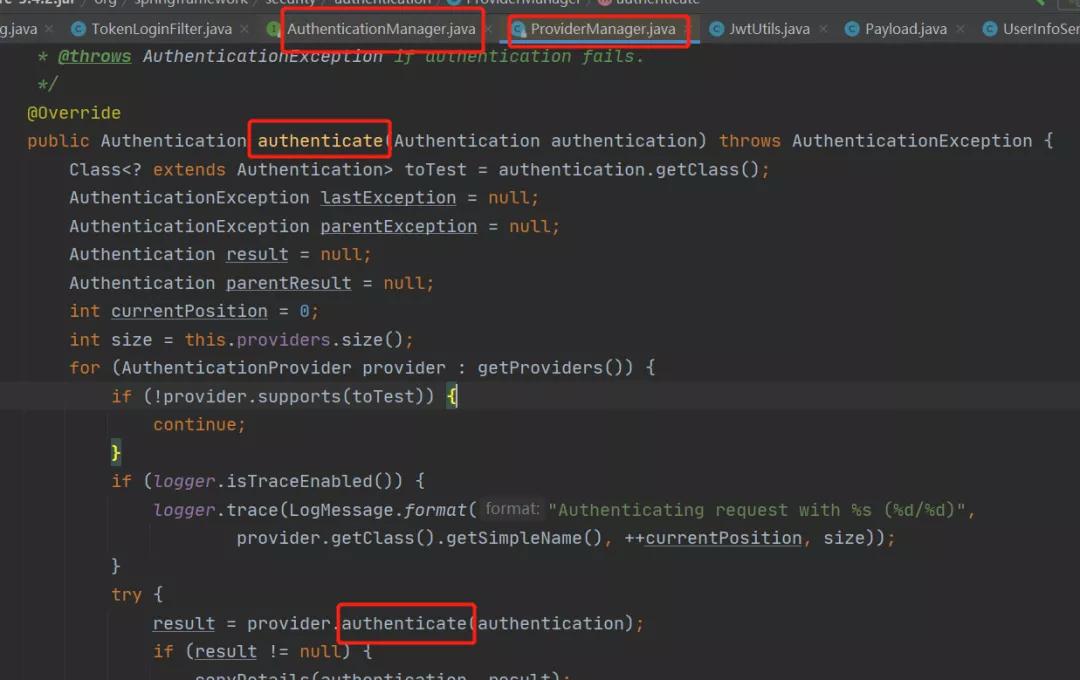
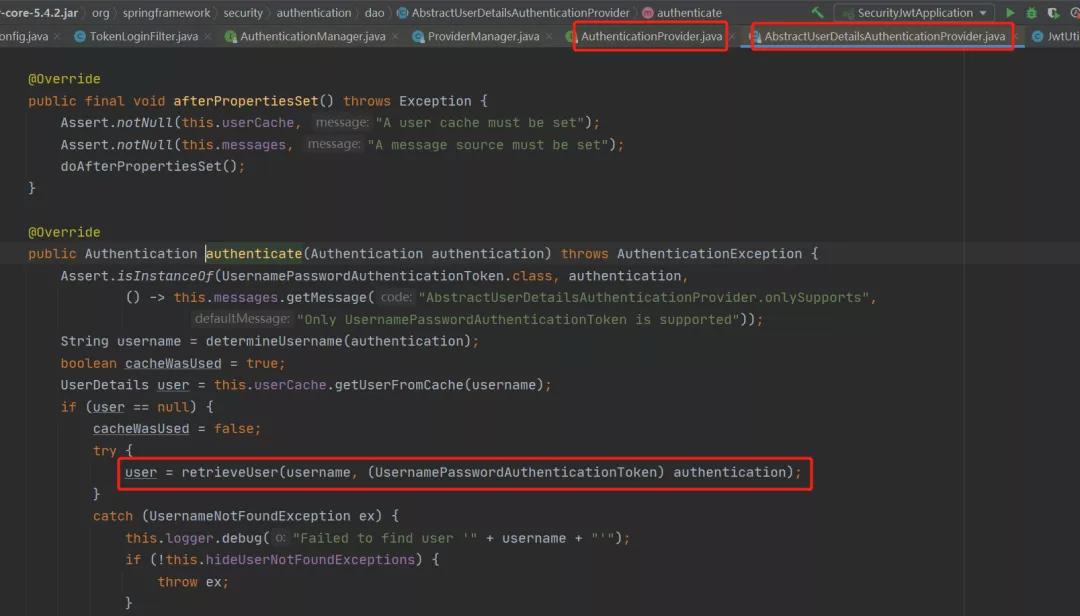
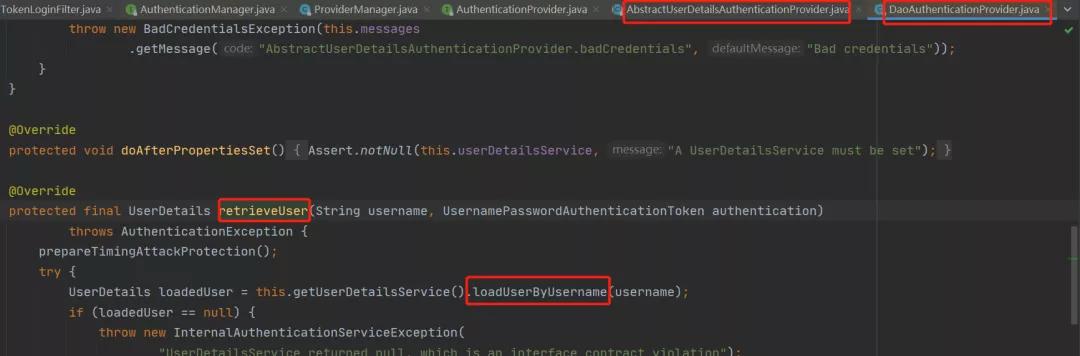
Security默認(rèn)登錄路徑為/login,當(dāng)我們調(diào)用該接口時(shí),它會(huì)調(diào)用上邊的attemptAuthentication方法;圖片圖片圖片圖片所以我們要自定義UserInfoService繼承UserDetailsService實(shí)現(xiàn)loadUserByUsername方法;
所以我們要自定義UserInfoService繼承UserDetailsService實(shí)現(xiàn)loadUserByUsername方法;
- public interface UserInfoService extends UserDetailsService {
- }
- @Service
- @Transactional
- public class UserInfoServiceImpl implements UserInfoService {
- @Autowired
- private SysUserInfoMapper userInfoMapper;
- @Override
- public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
- UserPojo user = userInfoMapper.queryByUserName(username);
- return user;
- }
- }
其中的loadUserByUsername返回的是UserDetails類(lèi)型,所以UserPojo繼承UserDetails類(lèi)
- @Data
- public class UserPojo implements UserDetails {
- private Integer id;
- private String username;
- private String password;
- private Integer status;
- private List<RolePojo> roles;
- @JsonIgnore
- @Override
- public Collection<? extends GrantedAuthority> getAuthorities() {
- //理想型返回 admin 權(quán)限,可自已處理這塊
- List<SimpleGrantedAuthority> auth = new ArrayList<>();
- auth.add(new SimpleGrantedAuthority("ADMIN"));
- return auth;
- }
- @Override
- public String getPassword() {
- return this.password;
- }
- @Override
- public String getUsername() {
- return this.username;
- }
- /**
- * 賬戶(hù)是否過(guò)期
- **/
- @JsonIgnore
- @Override
- public boolean isAccountNonExpired() {
- return true;
- }
- /**
- * 是否禁用
- */
- @JsonIgnore
- @Override
- public boolean isAccountNonLocked() {
- return true;
- }
- /**
- * 密碼是否過(guò)期
- */
- @JsonIgnore
- @Override
- public boolean isCredentialsNonExpired() {
- return true;
- }
- /**
- * 是否啟用
- */
- @JsonIgnore
- @Override
- public boolean isEnabled() {
- return true;
- }
- }
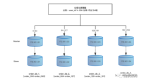
當(dāng)認(rèn)證通過(guò)之后會(huì)在SecurityContext中設(shè)置Authentication對(duì)象,回調(diào)調(diào)用successfulAuthentication方法返回token信息,
整體流程圖如下
鑒權(quán)流程
自定義token過(guò)濾器
- public class TokenVerifyFilter extends BasicAuthenticationFilter {
- private RsaKeyProperties prop;
- public TokenVerifyFilter(AuthenticationManager authenticationManager, RsaKeyProperties prop) {
- super(authenticationManager);
- this.prop = prop;
- }
- public void doFilterInternal(HttpServletRequest request, HttpServletResponse response, FilterChain chain) throws IOException, ServletException {
- String header = request.getHeader("Authorization");
- if (header == null || !header.startsWith("Bearer ")) {
- //如果攜帶錯(cuò)誤的token,則給用戶(hù)提示請(qǐng)登錄!
- chain.doFilter(request, response);
- } else {
- //如果攜帶了正確格式的token要先得到token
- String token = header.replace("Bearer ", "");
- //通過(guò)公鑰進(jìn)行解密:驗(yàn)證tken是否正確
- Payload<UserPojo> payload = JwtUtils.getInfoFromToken(token, prop.getPublicKey(), UserPojo.class);
- UserPojo user = payload.getUserInfo();
- if(user!=null){
- UsernamePasswordAuthenticationToken authResult = new UsernamePasswordAuthenticationToken(user.getUsername(), null, user.getAuthorities());
- //將認(rèn)證信息存到安全上下文中
- SecurityContextHolder.getContext().setAuthentication(authResult);
- chain.doFilter(request, response);
- }
- }
- }
- }
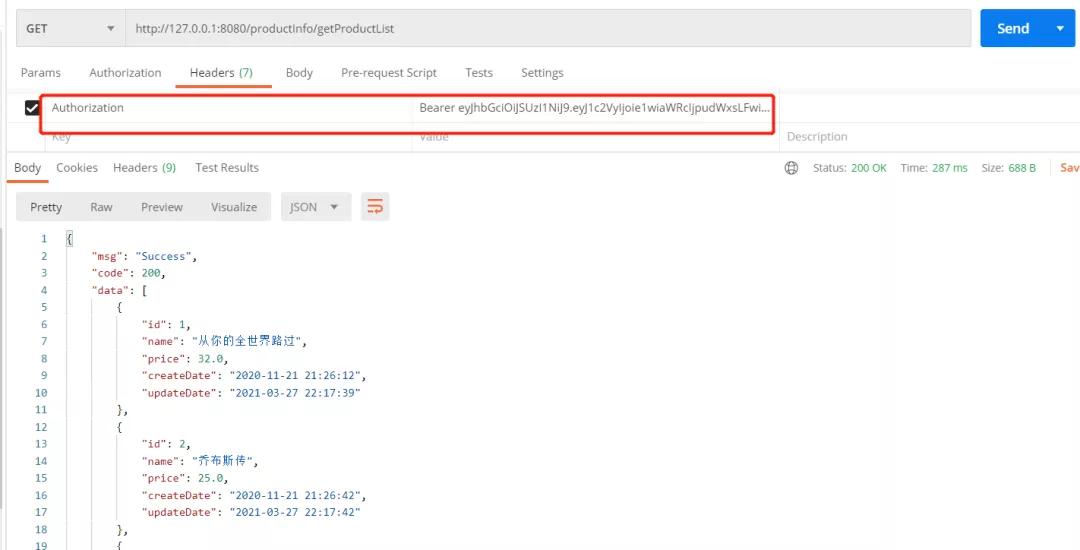
當(dāng)我們?cè)L問(wèn)時(shí)需要在header中攜帶token信息
本文轉(zhuǎn)載自微信公眾號(hào)「阿Q說(shuō)代碼」,可以通過(guò)以下二維碼關(guān)注。轉(zhuǎn)載本文請(qǐng)聯(lián)系阿Q說(shuō)代碼公眾號(hào)。